Category: Enterprise RAG
-
The Production Accountability Trap: Why Your RAG System Isn’t Ready for Enterprise AI Agents
Enterprise AI agents are moving from pilot projects to production systems that stakeholders expect to deliver measurable ROI. But here’s the uncomfortable truth: most RAG architectures powering these agents were designed for human queries, not autonomous agents making thousands of decisions per hour. The gap between expectation and reality is creating a production accountability crisis…
-
The Retrieval Adaptation Gap: Why Your Enterprise RAG Wastes 60% of Processing Power on One-Size-Fits-All Strategies
Your enterprise RAG system treats every query the same way. A simple factual lookup about “Q4 revenue targets” goes through the exact same retrieval pipeline as a complex analytical question about “comparative market positioning across three quarters with regulatory context.” Both hit your vector database, both perform full semantic reranking, both wait for the same…
-

The Hidden Cost Crisis in Enterprise RAG: Why Your Monitoring Stack Is Bleeding Budget Without You Knowing It
Every engineering leader running enterprise RAG systems faces the same invisible problem: they can’t see where their money is actually going. You’re tracking latency. You’re monitoring hallucinations. You’re measuring retrieval precision. But nobody in your organization can answer the most critical question: What does this retrieval cost per query, and how much are we wasting?…
-
The Fine-Tuning Illusion: Why Your Enterprise Should Abandon Static Models for Dynamic RAG
Your CTO walks into the boardroom with a $500K budget proposal: fine-tune your LLM on proprietary data to “lock in” company knowledge. It sounds strategic. It sounds permanent. It sounds like progress. But six weeks later, your legal team updates compliance policy, your product documentation ships with critical changes, and your expensively fine-tuned model is…
-

RAG Permission Management: The Overlooked Enterprise Blind Spot
Every day, enterprises deploy retrieval-augmented generation systems with confidence. Their benchmarks look pristine. Their latency metrics pass inspection. Their accuracy scores satisfy stakeholders. Yet somewhere in the quiet corners of their infrastructure, a silent catastrophe unfolds: unauthorized data access through RAG systems that have no concept of permission boundaries. This isn’t a theoretical problem. It’s…
-
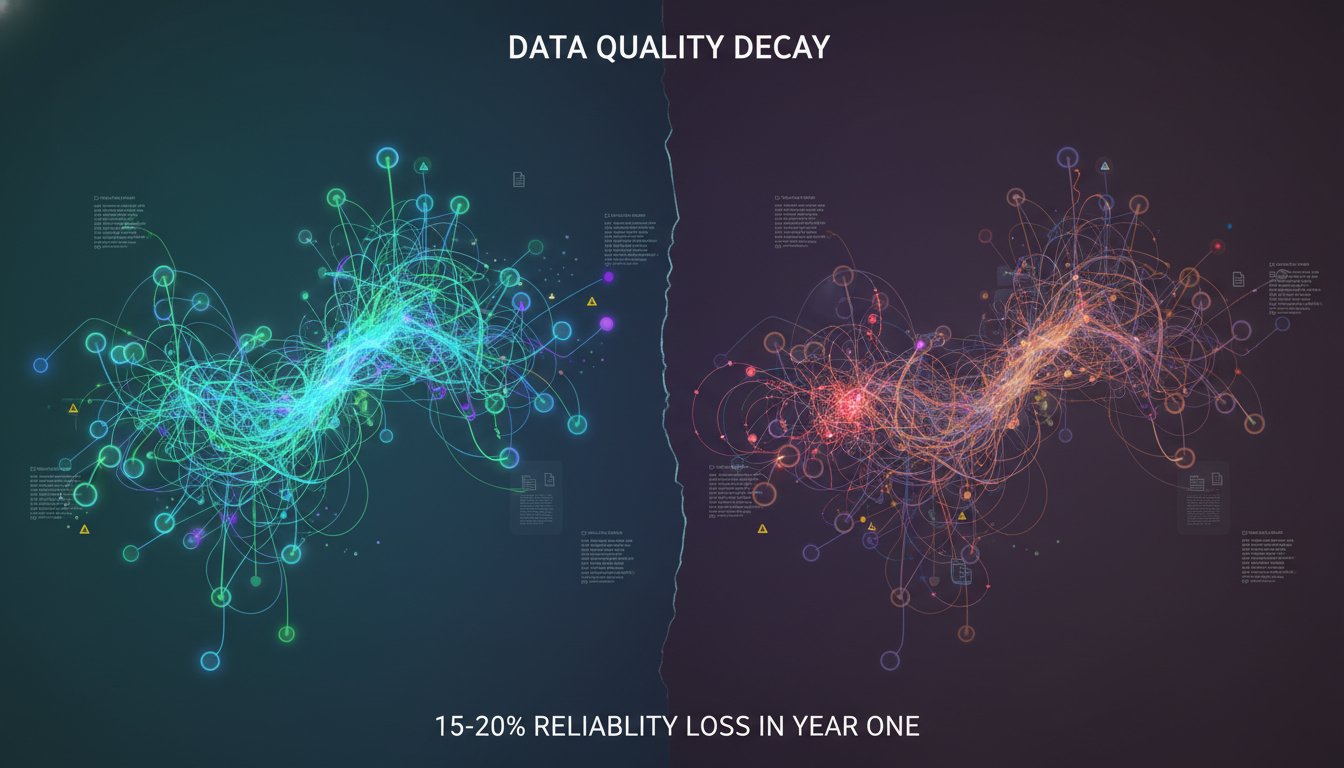
The Data Pipeline Silent Killer: Why Your RAG System’s Information Layer Is Rotting Without You Knowing
You deployed enterprise RAG six months ago. Performance was excellent at launch. Your retrieval accuracy was 89%, response latency hovered around 400ms, and the leadership team celebrated the rollout. Then, without warning, you noticed something strange: user satisfaction scores dropped 12% last month. Your team investigated the LLM model—no changes. They checked the retrieval infrastructure—no…
-
Permission-Based Retrieval at Scale: 3 Architectural Patterns That Protect Enterprise Data
Every enterprise RAG deployment faces the same critical question: How do you ensure your retrieval system respects user permissions without sacrificing performance at scale? The stakes couldn’t be higher. A financial services firm builds a sophisticated RAG system to synthesize market data, earnings reports, and regulatory filings. It works perfectly—until a junior analyst accidentally gets…
-

The Hidden Cost Crisis: Why 73% of Enterprise RAG Systems Are Hemorrhaging Money and How EraRAG Changes Everything
Last week, I watched a Fortune 500 CTO explain to his board why their $2.4 million RAG investment was delivering negative ROI. The culprit? Vector database costs that scaled “like a freight train hitting a brick wall.” His words, not mine. This isn’t an isolated incident. According to recent internal research, 72% of enterprise RAG…
